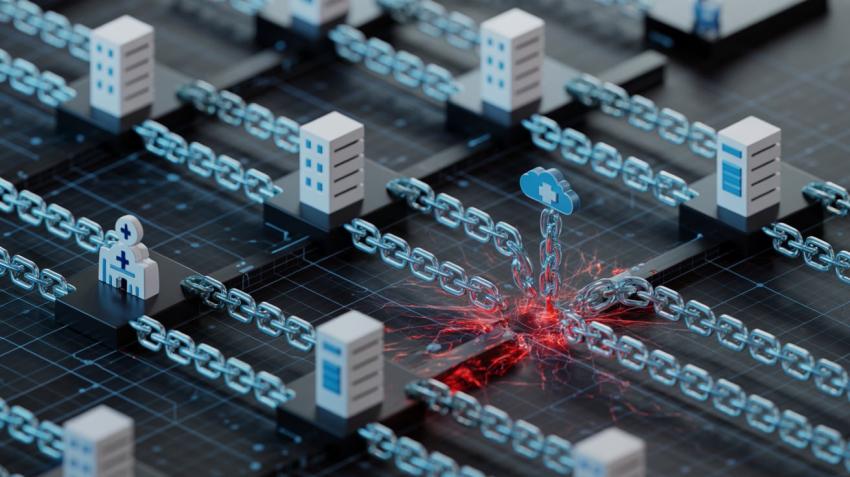
The healthcare industry has emerged as a primary industry for cybersecurity attacks, but interestingly enough, most of these breaches do not occur inside hospitals or clinics. In fact, the third-party vendors — those organizations that perform different tasks, such as billing or logistics or procurement of medical devices or IT services — those are what you're more likely to see breaches from. These third-party vendors are essential to providing healthcare, but in most cases their cybersecurity posture is not as robust as the healthcare facilities themselves. As such, they pose unique risk to patient data.
The Increasing Reliance on Vendors
Our healthcare system relies on a sprawling ecosystem of vendors. Vendors who perform diagnostics, software, supplies, and even insurance processing — they are woven into the very fabric of day-to-day operations. But as we continue to transform services away from in-person care to a digital landscape, the number and complexity of these vendor-vendor-vendor relationships will only increase. Each new vendor relationship only creates another place for attackers to enter the network directly or perhaps seize access to sensitive data.
The recent Data Breach involving Dealmed Medical Supplies highlights this increasing concern. Even though their business function is simply as a medical supplier — as opposed to a hospital or insurance company or payer — they still had personal data which was compromised. The lesson here is that even the perceived low-risk vendors can be valuable targets for hackers to access patient data through indirect means.
How Hackers Exploit Vendor Weaknesses
Cybercriminals know that many vendors do not have enterprise-level defenses. Rather than attacking a large healthcare organization with defenses like firewalls and monitoring systems, they will focus on smaller suppliers that are even less secure and may have older legacy systems. Once inside, they can steal data or utilize vendor access credentials to easily lateral into the larger system.
Common vulnerabilities are as follows:
- Unpatched software and legacy systems still in production
- Poor password hygiene, or shared credentials
- Inadequately encrypted data at rest or in transmission
- Minimal security vetting of subcontractors part of the vendor network
The continued risk is even worse as hospitals and vendors connect through cloud-based platforms and APIs. A minor intrusion can easily turn into a large-scale data breach exposing thousands of employees or patients to compromise.
The Compliance and Oversight Challenge
Although laws, like HIPAA, provide a structure for protecting patient data, enforcement across vendor networks is inconsistent. Many healthcare providers either do not conduct regular security audits of their vendors or neglect to request additional data protection language in contracts. It’s often a challenge to identify fault in the event of a breach occurring, and patients whose data is compromised often suffer the greatest consequences.
Steps Toward Stronger Vendor Security
To close these gaps, healthcare organizations must rethink how they manage third-party relationships.
Key strategies include:
Conducting annual cybersecurity risk assessments for all vendors.
Requiring third-party certifications (such as SOC 2 or HITRUST) before onboarding.
Implementing continuous monitoring of data exchanges and system access.
Establishing breach notification protocols and clear accountability in vendor contracts.
Adopting zero-trust architecture, assuming every external connection could be compromised.
A Shared Responsibility
Cybersecurity in healthcare extends beyond solely hospitals or IT departments — it is a shared responsibility of the entire service ecosystem. Every vendor that processes patient or employee data has a part in maintaining trust and integrity.
As evident in the Dealmed case and similar, a single weak link can compromise an entire network. While ensuring vendor security was previously an operational concern, it is now an essential element of ethical and responsible healthcare.